Windows Remote Desktop supports encryption. In the case of default configuration, Windows will sign a certificate by itself. But this certificate is obviously not trusted by default when the client connects.
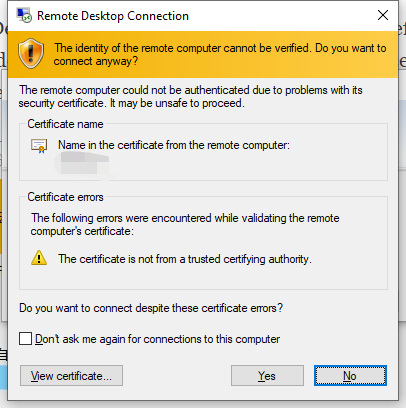
Although it is true that this self-signed certificate can be trusted on the client side. The disadvantage of this is that this self-signed certificate needs to be trusted once in various client devices. (For example, Microsoft's official Remote Desktop 8 in Android).
Because I use the certificate of let's encrypt, I note down how to set the certificate signed by let's encrypt to the server of windows remote desktop.
1. Preparation
A Let's encrypt certificate. I won't go into details about how to generate a certificate from Let's encrypt here. Here we just synchronize what the certificate should be. First of all, the certificates should all be pem certificates, and the certificate should obviously contain the domain name of the server machine. For example windows.xloypaypa.pub.
The certificates folder should contain the following:
.
├── cert.pem
├── chain.pem
├── fullchain.pem
├── privkey.pem
└── README
2. convert to pfx certificate
Pfx certificate is a certificate that contains both a public key and a private key. I personally don't know whether Windows Remote Desktop can use be configurated directly through a pair of pem certificate. But it is not difficult to convert to pfx anyway. All it takes is one line of command:
openssl pkcs12 -export -out certificate.pfx -inkey privkey.pem -in cert.pem -certfile chain.pem
And just give a password for above command.
3. Install the pfx certificate to the server
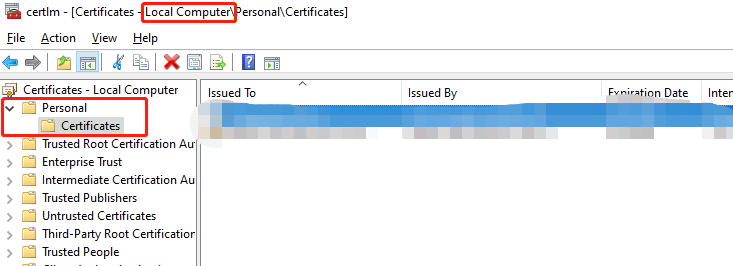
Copy the pfx certificate to the server and double-click. Then follow the instructions to import the certificate into "Certificates" in the "Personal" folder.
- Be careful to install the certificate to the local computer, not the current user.
- Put the certificate in "Personal"
Once finished, it should look like this (there is a certificate just now in the personal folder):
4. Update the remote desktop server configuration
Double-click the certificate on the right side of the certificate management to see the details of the certificate and get the thumbprint:
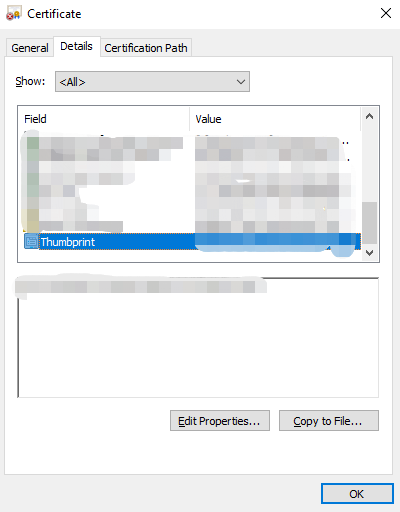
Then run in Powershell as administrator:
wmic /namespace:\\root\cimv2\TerminalServices PATH Win32_TSGeneralSetting Set SSLCertificateSHA1Hash="<The certificate fingerprint obtained above>"
At this point, the certificate configuration for Windows Remote Desktop Services is completed.